There has been a recent uptick in ATM attacks across the United States, particularly in multiple Western states. In many of these attacks, criminals have utilized never-before-seen ATM skimming devices and new methods.
In an era where digital transactions are omnipresent, ATM and ITM terminals have become prime targets for sophisticated criminal activities. Fraudulent schemes, including skimming, phishing, physical attacks and software hacking, are on the rise, posing significant threats to the security of financial transactions and personal data. The complexity and variability of these threats demand a security solution that is not only comprehensive but also adaptable to the evolving landscape of financial crime.

There are new and unique approaches against multiple types of ATM fraud.
New strategies extend beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics and proactive threat detection. The best approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI-based endpoint security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash-trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the host, attackers pursue objectives such as interception, eavesdropping, modification and impersonation.
There are even new cellular options available for remote sites and kiosks with secure VPNs.
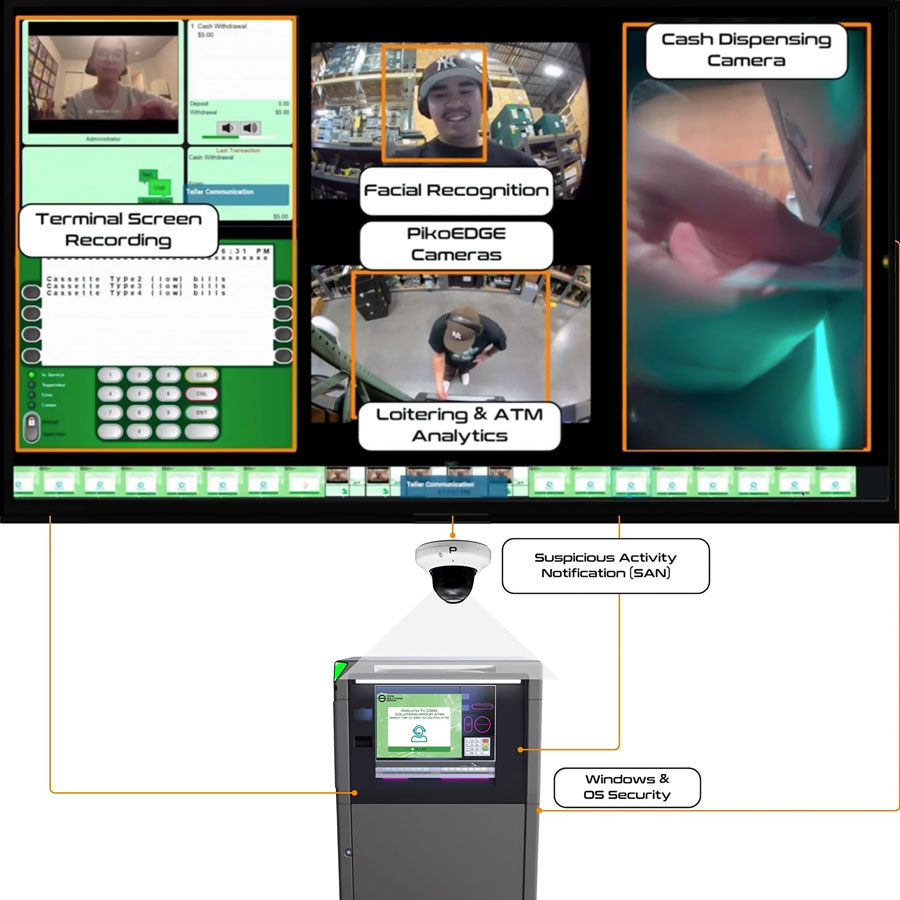
With today’s technology, ATM screen recording, strategic surveillance using overhead and ATM cameras, along with a dedicated cash dispensing camera, collaborate seamlessly to offer robust protection and valuable insights.
With ATM fraud up nearly 100%, this problem isn’t going away. The laundry list of types of ATM/ITM fraud stated previously continues to happen across the U.S. and by using new technology, automation, object detection and more, banks can protect themselves with a layered approach.